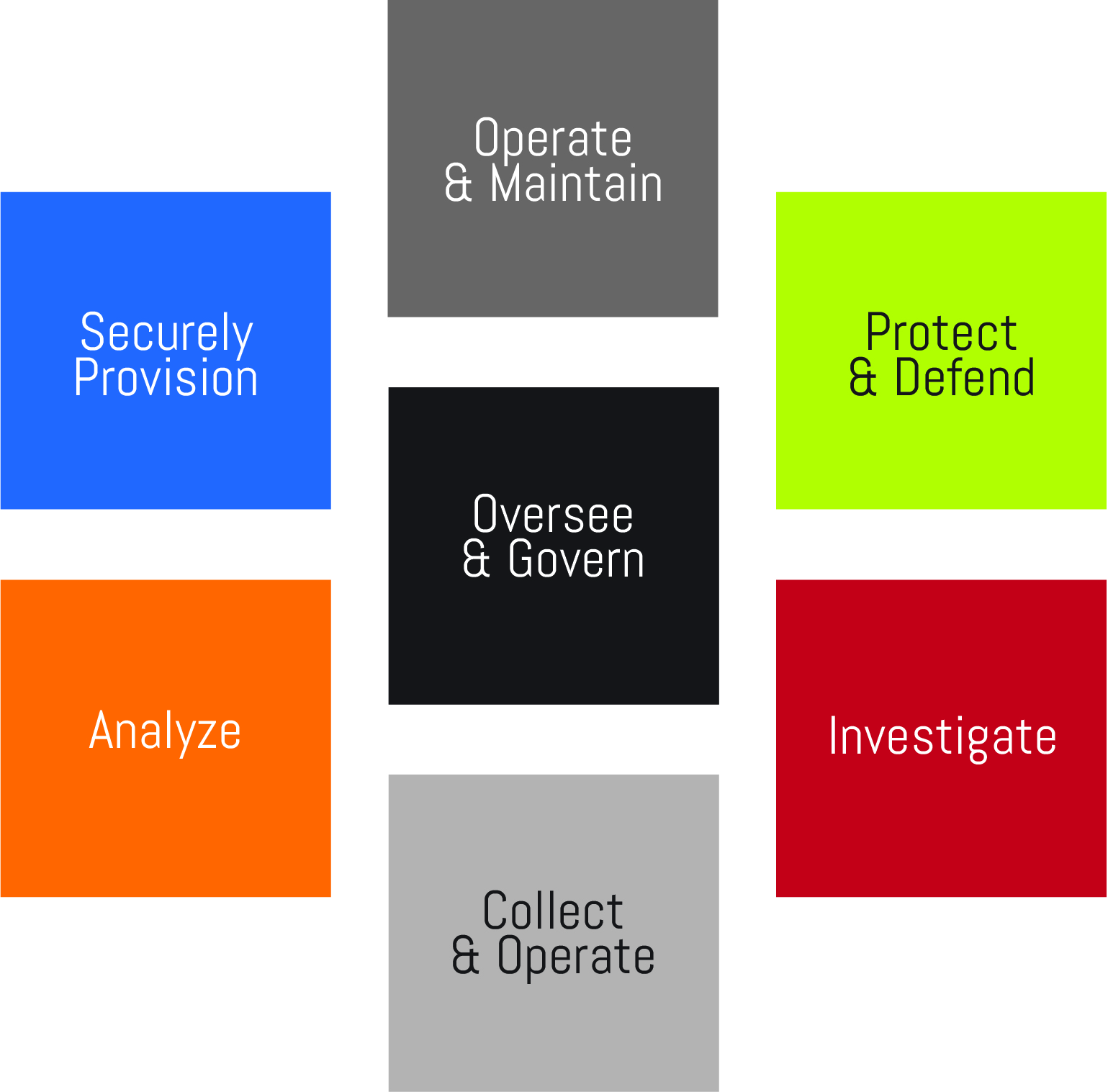
The CyberStronger Skills Assessment is carefully designed to meet the recommendations of the NICE Cybersecurity Workforce Framework (NCWF). NCWF is viewed as the “cybersecurity workforce dictionary,” providing the nationally recognized information and standards necessary to educate, recruit, train, develop, and retain a highly-qualified cyber security workforce.
NCWF identifies seven high-level categories of common cyber security functions. These provide the overarching structure of the NCWF. These categories are further divided into work roles. The NCWF also identifies specific competencies and related knowledge, skills, and abilities (KSAs) expected of a professional working in one of the identified work roles.
CYBRScore Skills Assessments utilize the NCWF recommendations to provide a performance-based assessment solution for employers seeking to evaluate their current workforce and position candidates.